-
Posts
141 -
Joined
-
Last visited
Content Type
Profiles
Forums
Downloads
Store
Everything posted by kennylovecode
-
Hi everyone, I am writing my own source code server recently. In this process, I may want to write some portable tools, such as importing the client's Itemtype.dat into my cq_itemtype table with one click. But I hope I can't find the decryption code resources for this.
-

NameChange Packet Question With En Conquer 5700?
kennylovecode replied to kennylovecode's topic in Conquer Online
AhA.....I just forgot! Actually, I just thought of refreshing the character's name when logging in, and sending an ANSWER_OK message packet to complete the process. code like this user.Send(new MsgServer.MsgMessage("ANSWER_OK", "ALLUSERS", MsgMessage.MsgColor.red, MsgMessage.ChatMode.Dialog).GetArray(stream)); user.ClientFlag |= msgserver.client.ServerFlag.AcceptLogin; user.Send(stream.LoginHandlerCreate(1, user.Player.Map)); MsgLoginHandler.LoadMap(user, stream); Of course, everyone's source code structure is different, so you need to test it yourself. -

NameChange Packet Question With En Conquer 5700?
kennylovecode replied to kennylovecode's topic in Conquer Online
Closed!!! [This forum has really inspired me a lot. Every time I post a question here, the next second I find the answer to solve it] -
Recently, I have been trying to develop a source code project from scratch, with a reference target version of 5700. I have collected some packet structures from many source codes. At present, I have been able to change the player name online. I found that after changing the name, I sent a Spawn packet to all players, which is a packet with type ID=10017. Everyone except myself can see the changed name, while the character name on my own screen remains unchanged. I'm not quite sure if I need to send a specific packet to update my role name. I have checked the source code of other authors regarding name changes.They seem to have all implemented measures to force players to log in offline and then log in again But what I want to do is not go offline, update my name in real time. Does the client version support it? Do you need special packet?
-

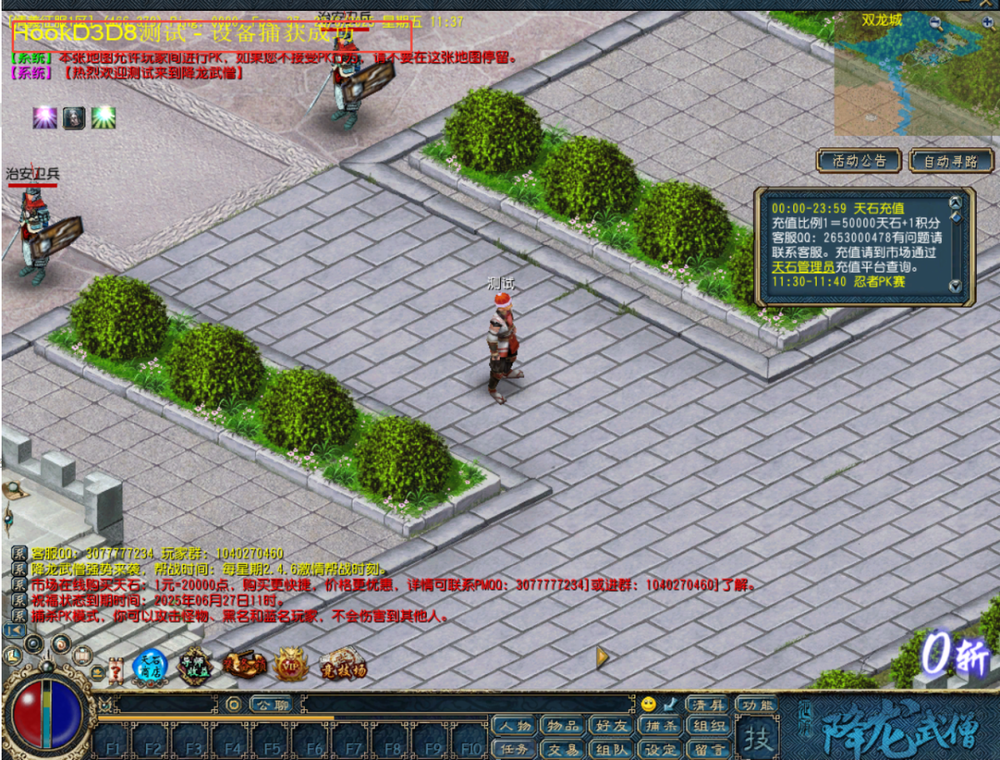
How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
Let's do some cool things together -

How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
I think this is the right direction, just like what open-source communities like GitHub are doing. You've actually been doing this kind of thing for a long time, open-sourcing many projects and compiling some resources, including your ConquerWiki. But you'll find that this doesn't attract much fresh blood, because the developers for this Conquer game are almost fixed, and very few people are interested in the game, let alone those who would study it. -

How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
But I don't know why they didn't do so. It seems that sharing is an obligation, and it rarely brings something valuable because people lack motivation. -

How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
So the community problem with the free system is that they don't need to put in any effort to receive the fruits of your labor and share them. In fact, I used to run a points community in my country, which required sharing and earning point rewards to exchange for other people's labor achievements. I think this is the only healthy and benign community... -

How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
Yes, actually I am willing to discuss and exchange these technologies, just as I have made some attempts and want to share them with everyone. But it seems that not many people are interested... -

How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
I just did some basic testing and successfully redrew. -

How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
As far as I know, most 2D version game clients are basically based on D3D8. If you have the capability, it can be changed to D3D9 or higher versions through hooking, but this requires deeper research -

How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
you can find it from "google", or github.com or anywhere if you search! Even you can ask CHATGPT for the download link to this file, and it can provide it to you completely, which is much better than asking on a forum, waiting, waiting, waiting, and then giving up. -

How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
What I am sharing is an idea of how to do it, not a complete project. But this idea is a feasible path that I have fully verified, not a hypothesis. There is an ancient Chinese saying that "teach him how to fish is better then just give a man a fish". I think this is very important. -

How to custom edit client with d3d8 hook
kennylovecode replied to kennylovecode's topic in Conquer Online
And Next. how to use your D3D8 hook to render a custom UI inside the game/client. Goal: Render Custom UI Over Game Screen We’ll do this by drawing inside the hkEndScene() function, which runs every frame right before the screen is presented. Prerequisites You must have: Already hooked EndScene (as we did above) Access to the LPDIRECT3DDEVICE8 pointer Initialized DirectX 8 properly in the target context Tools and Libraries (Optional) You can either: Use raw D3D8 drawing functions (simple, less dependency) Or use libraries like: ImGui + D3D8 backend (more complex, but easier to make UIs) D3DXFont / D3DXSprite (from d3dx8.lib) Let’s start with a raw example, then show how to add ImGui. Step-by-Step: Drawing Text and Boxes in hkEndScene 1. Draw Text with D3DXFont LPD3DXFONT pFont = nullptr; HRESULT APIENTRY hkEndScene(LPDIRECT3DDEVICE8 pDevice) { if (!pFont) { D3DXCreateFont(pDevice, 20, 0, FW_NORMAL, 1, FALSE, DEFAULT_CHARSET, OUT_DEFAULT_PRECIS, ANTIALIASED_QUALITY, DEFAULT_PITCH | FF_DONTCARE, "Arial", &pFont); } RECT rect = { 10, 10, 300, 300 }; pFont->DrawTextA(NULL, "Hello from Hook!", -1, &rect, DT_NOCLIP, D3DCOLOR_ARGB(255, 255, 0, 0)); return oEndScene(pDevice); } This renders “Hello from Hook!” in red text at the top-left of the screen. 2. Draw a Filled Rectangle (Box) void DrawBox(LPDIRECT3DDEVICE8 pDevice, float x, float y, float width, float height, D3DCOLOR color) { struct Vertex { float x, y, z, rhw; DWORD color; }; Vertex vertices[] = { { x, y, 0.0f, 1.0f, color }, { x + width, y, 0.0f, 1.0f, color }, { x, y + height, 0.0f, 1.0f, color }, { x + width, y + height, 0.0f, 1.0f, color }, }; pDevice->SetRenderState(D3DRS_LIGHTING, FALSE); pDevice->SetRenderState(D3DRS_ZENABLE, FALSE); pDevice->SetFVF(D3DFVF_XYZRHW | D3DFVF_DIFFUSE); pDevice->DrawPrimitiveUP(D3DPT_TRIANGLESTRIP, 2, vertices, sizeof(Vertex)); } // Inside hkEndScene DrawBox(pDevice, 50, 50, 100, 20, D3DCOLOR_ARGB(150, 0, 255, 0)); // semi-transparent green box Bonus: Show Health Bar Above Entity Assuming you know the screen position (x, y) of the entity, you can do: float healthPercent = 0.7f; // 70% health DrawBox(pDevice, x, y - 10, 50, 5, D3DCOLOR_ARGB(150, 0, 0, 0)); // background DrawBox(pDevice, x, y - 10, 50 * healthPercent, 5, D3DCOLOR_ARGB(200, 0, 255, 0)); // foreground Optional: Use ImGui for Modern UI ImGui works with D3D8 too, with slight setup. You’ll need: ImGui D3D8 backend (use imgui_impl_dx8.cpp) Windows message handler (imgui_impl_win32.cpp) In hkEndScene: ImGui_ImplDX8_NewFrame(); ImGui_ImplWin32_NewFrame(); ImGui::NewFrame(); ImGui::Begin("Custom UI"); ImGui::Text("Injected Overlay!"); ImGui::End(); ImGui::Render(); ImGui_ImplDX8_RenderDrawData(ImGui::GetDrawData()); Debug Tips Ensure EndScene is being called (log or breakpoint) Use OutputDebugString or write to file for diagnostics If the overlay doesn’t show: Make sure the render state is correct The game window must be the foreground window (for some methods) Try drawing solid rectangles first (not text) Summary FeatureMethod TextD3DXCreateFont, DrawTextA Box/RectanglesCustom vertex arrays + DrawPrimitiveUP UIImGui (with D3D8 backend) Health BarCombine rectangles and entity coordinates -
Here's a full D3D8 Hook Tutorial in English, including all steps from knowledge prerequisites to debugging and logging. 1. Prerequisites Before diving into D3D8 hooking, you should be familiar with the following: TopicDescription C/C++ ProgrammingKnow classes, pointers, function pointers DLL BasicsUnderstand how DLLs work and are injected Windows APIBasic Win32 programming and message loop Assembly & MemoryBasic understanding of memory layout and vtables DirectX 8 ConceptsHow Direct3D8 renders (e.g., EndScene, Reset) 2. Required Tools ToolPurposeRecommendation Visual Studio 2019/2022Build and debug C++ projects DirectX 8 SDKProvides d3d8.h, d3d8.lib, etc. DLL InjectorInject your DLL into the target process[Extreme Injector, Process Hacker, or custom one] Cheat EngineMemory inspection/debugging DebugView or file loggerFor logging without a console 3. Create the Hook DLL Project 3.1 Set up a Visual Studio Project Open Visual Studio → Create New Project → C++ Dynamic-Link Library (DLL) Name it something like D3D8Hook Set Project Properties: C/C++ > General > Additional Include Directories: Add the DirectX SDK Include path Linker > Input > Additional Dependencies: Add d3d8.lib, d3dx8.lib 3.2 Write the Hooking Code // D3D8Hook.cpp // D3D8Hook.cpp #include <Windows.h> #include <d3d8.h> #include <d3dx8.h> typedef HRESULT(APIENTRY* EndScene_t)(LPDIRECT3DDEVICE8 pDevice); EndScene_t oEndScene = nullptr; DWORD WINAPI MainThread(LPVOID); // Hook implementation HRESULT APIENTRY hkEndScene(LPDIRECT3DDEVICE8 pDevice) { static bool once = false; if (!once) { MessageBoxA(0, "D3D8 Hooked!", "Success", MB_OK); once = true; } return oEndScene(pDevice); // Call the original } void HookFunction() { IDirect3D8* pD3D = Direct3DCreate8(D3D_SDK_VERSION); if (!pD3D) return; D3DPRESENT_PARAMETERS d3dpp = {}; d3dpp.Windowed = TRUE; d3dpp.SwapEffect = D3DSWAPEFFECT_DISCARD; d3dpp.hDeviceWindow = GetForegroundWindow(); IDirect3DDevice8* pDevice = nullptr; if (SUCCEEDED(pD3D->CreateDevice(D3DADAPTER_DEFAULT, D3DDEVTYPE_HAL, d3dpp.hDeviceWindow, D3DCREATE_SOFTWARE_VERTEXPROCESSING, &d3dpp, &pDevice))) { void** vtable = *(void***)pDevice; oEndScene = (EndScene_t)vtable[35]; DWORD oldProtect; VirtualProtect(&vtable[35], sizeof(void*), PAGE_EXECUTE_READWRITE, &oldProtect); vtable[35] = (void*)&hkEndScene; VirtualProtect(&vtable[35], sizeof(void*), oldProtect, &oldProtect); pDevice->Release(); } pD3D->Release(); } DWORD WINAPI MainThread(LPVOID) { HookFunction(); return 0; } BOOL APIENTRY DllMain(HMODULE hModule, DWORD reason, LPVOID) { if (reason == DLL_PROCESS_ATTACH) CreateThread(nullptr, 0, MainThread, nullptr, 0, nullptr); return TRUE; } 3.3 Build the DLL Use Build → Build Solution (Ctrl + Shift + B) and find the DLL in: csharp 复制编辑 [YourProjectFolder]\x86\Debug\D3D8Hook.dll Make sure it's compiled for x86 if the target process is 32-bit. 4. Injecting the DLL Method 1: Use an Injector Tool Start the game or D3D8-based application Open an injector (e.g., Extreme Injector or Process Hacker) Select the target process and inject D3D8Hook.dll Method 2: Write Your Own Injector (optional) cpp 复制编辑 HANDLE hProc = OpenProcess(PROCESS_ALL_ACCESS, FALSE, targetPID); LPVOID addr = VirtualAllocEx(hProc, NULL, len, MEM_COMMIT, PAGE_READWRITE); WriteProcessMemory(hProc, addr, dllPath, len, NULL); CreateRemoteThread(hProc, NULL, 0, (LPTHREAD_START_ROUTINE)LoadLibraryA, addr, 0, NULL); 5. Debugging and Logging 5.1 Output to DebugView Use this to see logs: cpp 复制编辑 OutputDebugStringA("D3D8 Hook initialized!"); You can view logs with DebugView by Sysinternals. 5.2 Write Logs to File cpp 复制编辑 void Log(const char* msg) { FILE* f = fopen("C:\\D3D8_Hook_Log.txt", "a+"); if (f) { fprintf(f, "%s\n", msg); fclose(f); } } 5.3 Use Visual Studio Debugger Build your DLL in Debug mode Launch the target app Attach Visual Studio (Debug → Attach to Process) Set breakpoints in hkEndScene or elsewhere Common Issues & Fixes IssuePossible Cause Game crashesWrong vtable index or uninitialized pointers Nothing happensHook not applied or wrong process architecture DLL fails to injectMissing dependencies or wrong platform (x64 vs x86)
-
-
i think so.
-
I'm also in the process of learning, I've just analyzed its method but haven't gone through the process and results yet. But I've analyzed about 4-5 sample clients, and they are almost all done this way.
-
Since you have already seen which table the mapping is for, you can certainly try adding this column to the table to test
-
Some thing for learning .... for long time forget mark D3D8 HOOK: // Typedef of reset and present HRESULT __stdcall nReset ( LPDIRECT3DDEVICE8 pDevice, D3DPRESENT_PARAMETERS* pPresentationParameters ); typedef HRESULT ( APIENTRY* Reset_t ) ( LPDIRECT3DDEVICE8 pDevice, D3DPRESENT_PARAMETERS* pPresentationParameters ); Reset_t pReset; HRESULT __stdcall nPresent ( LPDIRECT3DDEVICE8 pDevice,CONST RECT* pSourceRect,CONST RECT* pDestRect,HWND hDestWindowOverride,CONST RGNDATA* pDirtyRegion ); typedef HRESULT ( APIENTRY* Present_t)( LPDIRECT3DDEVICE8 pDevice,CONST RECT* pSourceRect,CONST RECT* pDestRect,HWND hDestWindowOverride,CONST RGNDATA* pDirtyRegion ); Present_t pPresent; HRESULT __stdcall nReset ( LPDIRECT3DDEVICE8 pDevice , D3DPRESENT_PARAMETERS* pPresentationParameters ) { _asm PUSHAD; Tools.AddLog("Hook Reset\n"); _asm POPAD; return pReset(pDevice, pPresentationParameters); } HRESULT __stdcall nPresent ( LPDIRECT3DDEVICE8 pDevice,CONST RECT* pSourceRect, CONST RECT* pDestRect, HWND hDestWindowOverride, CONST RGNDATA* pDirtyRegion ) { _asm PUSHAD; Tools.AddLog("Hook Present\n"); _asm POPAD; return pPresent (pDevice, pSourceRect, pDestRect, hDestWindowOverride, pDirtyRegion); } DWORD_PTR * Hook :: FindDevice ( DWORD Base, DWORD Len ) { unsigned long i = 0, n = 0; for( i = 0; i < Len; i++ ) { if(*(BYTE *)(Base+i+0x00)==0xC7)n++; if(*(BYTE *)(Base+i+0x01)==0x06)n++; if(*(BYTE *)(Base+i+0x06)==0x89)n++; if(*(BYTE *)(Base+i+0x07)==0x86)n++; if(*(BYTE *)(Base+i+0x0C)==0x89)n++; if(*(BYTE *)(Base+i+0x0D)==0x86)n++; if( n == 6 ) return ( DWORD_PTR * ) ( Base + i + 2 ); n = 0; } return(0); } int __fastcall StaticHook ( void ) { HMODULE hD3D8Dll; do{ Tools.AddLog("%s - Loading d3d8.dll->",Tools.AddTime()); hD3D8Dll = GetModuleHandle("d3d8.dll"); Sleep(20); Tools.AddLog("OK!\n"); } while(!hD3D8Dll); Tools.AddLog("%s - Enable Device [Metin2]->",Tools.AddTime()); DWORD_PTR * VtablePtr = cHook.FindDevice((DWORD)hD3D8Dll,0x128000); Tools.AddLog("OK!\n"); if ( VtablePtr == NULL ) { MessageBox(NULL,"Device Not Found !! Please try again",0,MB_ICONSTOP); ExitProcess(TRUE); } Tools.AddLog("%s - Type Device->",Tools.AddTime()); DWORD_PTR* VTable = 0; *(DWORD_PTR*)&VTable = *(DWORD_PTR *)VtablePtr; Tools.AddLog("OK!\n"); Tools.AddLog("%s - Hooking Class->",Tools.AddTime()); pPresent = (Present_t) Tools.bDetourA((PBYTE)VTable[15],(LPBYTE)nPresent,6); pReset = (Reset_t) Tools.bDetourA((PBYTE)VTable[14],(LPBYTE)nReset,6); Tools.AddLog("OK!\n"); return(0); } bool __stdcall DllMain ( HMODULE hDll, unsigned long Reason , LPVOID LPReserved ) { DisableThreadLibraryCalls(hDll); switch ( Reason ) { case DLL_PROCESS_ATTACH : CreateThread(0,0,(LPTHREAD_START_ROUTINE)StaticHoo k ,0,0,0); break; case DLL_PROCESS_DETACH : break; } return (1); } d3d9 hook: // Typedef of reset and present HRESULT __stdcall nReset ( LPDIRECT3DDEVICE9 pDevice, D3DPRESENT_PARAMETERS* pPresentationParameters ); typedef HRESULT ( APIENTRY* Reset_t ) ( LPDIRECT3DDEVICE8 pDevice, D3DPRESENT_PARAMETERS* pPresentationParameters ); Reset_t pReset; HRESULT __stdcall nPresent ( LPDIRECT3DDEVICE9 pDevice,CONST RECT* pSourceRect,CONST RECT* pDestRect,HWND hDestWindowOverride,CONST RGNDATA* pDirtyRegion ); typedef HRESULT ( APIENTRY* Present_t)( LPDIRECT3DDEVICE9 pDevice,CONST RECT* pSourceRect,CONST RECT* pDestRect,HWND hDestWindowOverride,CONST RGNDATA* pDirtyRegion ); Present_t pPresent; HRESULT __stdcall nReset ( LPDIRECT3DDEVICE9 pDevice , D3DPRESENT_PARAMETERS* pPresentationParameters ) { _asm PUSHAD; Tools.AddLog("Hook Reset\n"); _asm POPAD; return pReset(pDevice, pPresentationParameters); } HRESULT __stdcall nPresent ( LPDIRECT3DDEVICE9 pDevice,CONST RECT* pSourceRect, CONST RECT* pDestRect, HWND hDestWindowOverride, CONST RGNDATA* pDirtyRegion ) { _asm PUSHAD; Tools.AddLog("Hook Present\n"); _asm POPAD; return pPresent (pDevice, pSourceRect, pDestRect, hDestWindowOverride, pDirtyRegion); } DWORD_PTR * Hook :: FindDevice ( DWORD Base, DWORD Len ) { unsigned long i = 0, n = 0; for( i = 0; i < Len; i++ ) { if(*(BYTE *)(Base+i+0x00)==0xC7)n++; if(*(BYTE *)(Base+i+0x01)==0x06)n++; if(*(BYTE *)(Base+i+0x06)==0x89)n++; if(*(BYTE *)(Base+i+0x07)==0x86)n++; if(*(BYTE *)(Base+i+0x0C)==0x89)n++; if(*(BYTE *)(Base+i+0x0D)==0x86)n++; if( n == 6 ) return ( DWORD_PTR * ) ( Base + i + 2 ); n = 0; } return(0); } int __fastcall StaticHook ( void ) { HMODULE hD3D9Dll; do{ Tools.AddLog("%s - Loading d3d9.dll->",Tools.AddTime()); hD3D9Dll = GetModuleHandle("d3d9.dll"); Sleep(20); Tools.AddLog("OK!\n"); } while(!hD3D9Dll); Tools.AddLog("%s - Enable Device d3d9->",Tools.AddTime()); DWORD_PTR * VtablePtr = cHook.FindDevice((DWORD)hD3D9Dll,0x128000); Tools.AddLog("OK!\n"); if ( VtablePtr == NULL ) { MessageBox(NULL,"Device Not Found !! Please try again",0,MB_ICONSTOP); ExitProcess(TRUE); } Tools.AddLog("%s - Type Device->",Tools.AddTime()); DWORD_PTR* VTable = 0; *(DWORD_PTR*)&VTable = *(DWORD_PTR *)VtablePtr; Tools.AddLog("OK!\n"); Tools.AddLog("%s - Hooking Class->",Tools.AddTime()); pPresent = (Present_t) Tools.bDetourA((PBYTE)VTable[17],(LPBYTE)nPresent,6); pReset = (Reset_t) Tools.bDetourA((PBYTE)VTable[16],(LPBYTE)nReset,6); Tools.AddLog("OK!\n"); return(0); }
-
copy map dir from client!
-
1. Use Dear ImGui & D3D9Hook 2. Dev Custom client GUI 3. overlay old client gui This is a classic client modification case that uses ImGUI to overwrite a large amount of the original UI
-
No, it's actually just removing some GUI configurations from the client and changing the GUI to a nostalgic theme. This isn't a lie, because I've also tried it, and it's feasible.
-
Although I haven't used this source, I seem to have seen its version number somewhere. You can try using the v5517 version client and loader to test.
-
I've been saving this playlist for a long time, kept looking but never understood it I really don't have a talent for decompilation; assembly code looks like machine code to me 01010101010.... Actually, I've been studying how to modify all player characters in the client with health bars through assembly code... obviously, I failed Because I really don't have a lot of time to spend on studying this, but I've seen many clients do it this way and succeed